Digital Communication Technologies (DCT)
What are Digital Communication Technologies
DCT's are digital tools that allow two or more people to communicate with one another. These can be written, verbal, visual or audible communication. Some examples of these are:
- Having a text conversation with someone via mobile phone
- Using Facebook or Twitter to keep in touch with family or friends
- Collaborating on a wiki or a blog to with students in a work group
|
Electronic mail, known as email, is the sending and receiving of messages electronically over the Internet. Email has been in use for over 25 years and is the most widely used Internet tool. Email has evolved from being a fixed communication tool between one computer and another, and can now be accessed via portable devices such as cell phones, MP3 players, tablets and more. This is only made possible through the use of wireless internet cards built into these devices. Email is a software technology that requires the use of a computer or mobile device (hardware technology).
|
http://www.therealtimscott.com/
|
Short Message Service (SMS)
The term short message service is often referred to as texting. Texting is most commonly used for short messages. However with the use of software SMS can now be used from PC to Cellphone, Iphone etc. SMS is a hardware technology that is used on a cellphone however can be a software technology if used via a PC.
Multimedia Messaging Service (MMS)
The term multimedia message service is often referred to as pxting. This is where a text message is accompanied with an image, small video file or sound bite.
This is a newer technology and older cellphones may not be able to support MMS. MMS is also a hardware technology. |
http://www.fusion92.com
|
Voice-over-Internet Protocol (VoIP)
Voice-over-internet Protocols is generally a range of technologies that allows verbal communication over the Internet. The most obvious example of this is the program Skype. Other examples like using voice chat in MSN , G Talk or Yahoo messenger can be regarded as VoIP. To talk to someone using MSN, the person at the other end also needs MSN. The same applies to Yahoo and, to a great extent, to Skype. They use their own special system that isn't open and won't connect to other systems easily. VoIPs are software technologies often used on a computer but now also available on mobile devices.
Chat & Instant Messaging
Chat is the name given to “real time” (as it happens) online communication. It is a series of typed messages between two or more people. The response time can be immediate, but there can be a few seconds delay depending on how busy the internet is and the number of people using chat. Chat rooms are sometimes included as a feature of a Web site, where users can log into the "chat room" to exchange comments and information about the topics on the site.
Instant messaging is a new variation of chat. It allows a user to have a list of contacts (who also use the service) The instant messaging software displays which of your contacts are currently online and available to chat. You need specific chat software such as MSN Messenger, which is supplied with the Windows operating system, others are ICQ, Yahoo chat and Google chat. You will need to register a login name and password to use chat.
Instant messaging is a new variation of chat. It allows a user to have a list of contacts (who also use the service) The instant messaging software displays which of your contacts are currently online and available to chat. You need specific chat software such as MSN Messenger, which is supplied with the Windows operating system, others are ICQ, Yahoo chat and Google chat. You will need to register a login name and password to use chat.
Exercise
Download and print the file below and complete the exercise.
| dct_exercise_1.pdf | |
| File Size: | 168 kb |
| File Type: | |
Social Media
What is social media? Social media are primarily Internet and mobile-based tools for sharing and discussing information among human beings. The term most often refers to activities that integrate technology and the construction of words, pictures, videos and audio. Social Media is a tool that is used both on a personal level and organisational and corporate level. Social Media and Websites are also software technologies that run off hardware technologies like computers and cellphones.
For many of these services you will need to register or sign up to them and in some case download the software to run them. Most of these services will require an email address to register to. All of these services require the internet to access them and they can be accessed via computer, laptop, cellphone, iphone, ipad, ipod, blackberry and more. Setting up an email account and registering with these service will be explained further down the page.
Social Media in Plain English
http://commoncraft.com/
Blogs, Wikis and Internet Forums
Blogs, Wikis and Forums are all internet based tools to allow people to communicate with one another usually around a specific topic or interest. These tools are usually free for people to use and will usually require an email address to register. Blogs, Wikis, and Forums can be used as a personal way to express yourself and your interests to the world or to share knowledge and opinions with other like minded people. For example the CLC Tips & Tricks Blog is a blog that provides free computer and technology related tips, tricks and advice.
Examples and explanations of Blogs, Wikis, and Forums
Examples and explanations of Blogs, Wikis, and Forums
|
|
|
View the student forum and introduce yourself. You will need an email address to post a comment. Click Here Student Forum
Websites
The web has been around for some time now and many businesses have incorporated a website as part of their operations. A website is another way that an organisation can communicate with their customers or potential customers. Organisations primarily used websites to advertise products and services. However today, organisations use websites to sell products and services through online shopping and offer online support to customers.
Websites are also used and created by individuals who wish to tell others about themselves or to provide information on topics of interest.
Websites are also used and created by individuals who wish to tell others about themselves or to provide information on topics of interest.
Exercise
Download and print the file below and complete the exercise.
| dct_exercise_2.pdf | |
| File Size: | 164 kb |
| File Type: | |
Purpose, Target audience and type of DCTs
Each type of digital communication technology has its own conventions. Conventions are accepted rules or standards for the communication tool. For example certain language will be acceptable in some DCTs and not in others. Language like "R, B4, LOL, U" are all acceptable uses of communication for SMS or TXT DCTs and sometimes Twitter depending on the purpose. Other DCTs require full language communication such as email.
Email - Creating and Using Gmail
How to set up a Gmail Account
To create a Gmail account, click on this link - www.gmail.com
Use the video to assist you in creating your own Gmail account.
Use the video to assist you in creating your own Gmail account.
Email Conventions
Email has become one of the most widely used forms of DCTs, but many of its users are still unaware of the recognised conventions in terms of email etiquette and layout.
Email Etiquette
Email Etiquette
- Do not use all capitals as this represents a raised voice or SHOUTING
- Use a meaningful and relevant subject heading so that the recipient has some idea of what the email is about
- Consider the size of attachments before sending them as the recipient may not be able to view the attachment if they have a slow connection
- Be careful what you forward onto friends and who you forward them to. Chainmail is should never be forwarded onwards, you should simply delete them as soon as you see what they are. Joke emails can be dangerous as some my find it inappropriate
- If you are sending emails to multiple people at a time ensure you use the "BCC" (Blind Carbon Copy) option to enter the email addresses into instead of the "To" option. This is because this will not advertise the recipients email addresses to all of the recipients of the email, hereby keeping the privacy of your contacts.
For more email etiquette visit this website. http://www.101emailetiquettetips.com/
Composing an Email in Gmail
If you do not have any contacts in your email account, practice sending emails to [email protected]
Formatting Mail in Gmail
Attachments in Gmail
Practice attaching documents from your computer or the venue computers and sending them to [email protected]
Labels/Folders in Gmail
Adding Signatures in Gmail
Exercise
Download and print the file below and complete the exercise.
| dct_exercise_3.pdf | |
| File Size: | 168 kb |
| File Type: | |
Blogs - Creating and Using Blogs
Like email, Blogs have there own set of conventions and etiquette. If you are unsure what a Blog is return to the top of the page and watch the video on blogs.
Like email, Blogs have there own set of conventions and etiquette. If you are unsure what a Blog is return to the top of the page and watch the video on blogs.
Blog Etiquette
- Always respect copyright and intellectual property laws and regulations. Never copy peoples blog comments and claim them as your own, If you wish to use another persons comments either seek their approval or reference your source and original author. More information on Copyright earlier on this page and on the Internet Page.
- Think before you blog. Since blogs a public access, you must seriously consider your comments before posting them to avoid having comments on there that you may regret latter. Blogs can have an option of restricted access so keep that in mind when creating your blog.
- Don't be abusive. Due to the public nature of blogs, this does lead to the likely hood of disagreement on topics. If you find a comment that makes you angry. Avoid making comments that will incite comments of the abusive nature. Discussion is encouraged on blogs as long as the discussion is appropriate and not abusive. If you feel the need to critisise an opinion, ensure your comments are relevant to the opinion only and not the person voicing the opinion.
- Stick to the topic. When commenting on blogs ensure your comments a relevant to the blog post. If you think your comment may not be relevant start a new post.
- Don't respond to blog trolls. A "troll" is slang for a person who repeatedly posts messages on blogs that are not relevant to the topic. Avoid responding to these posts as this simply encourages the persons actions.
Creating a Blog using Weebly
Weebly is a fast and easy free online website and blog builder. We will show you how to create a free blog with Weebly. Click on this link or type the URL into your web browser www.weebly.com
First you need to sign up to weebly, the page below will display. Note: you will need a email account before signing up. Look above for instructions on creating a gmail account.
First you need to sign up to weebly, the page below will display. Note: you will need a email account before signing up. Look above for instructions on creating a gmail account.
- Enter a user name into the first box
- Enter a unique password
- Enter your Email account.
- Check the Terms of Service and then click Sign Up
|
First set up instructions, click on this link - First-steps
|
|
Once you have completed the first steps you will be ready to choose a theme.
Choosing Themes, Click on this link for instructions on choosing a theme. - Choosing Themes |
|
Editing your header, Click on this link for instructions to edit your header - Edit Header
|
|
Creating a Blog Page, click on this link - Creating a Blog page
|
Now you have succesfully created a blog, you may want to edit it. Click on the CLC Tips & Tricks Blog for an example of a fully functioning blog.
For instructions on how to edit and add blog posts to your blog click on this link. Blogs & Forums
Navigate to this website for more tips on creating a Weebly web page and blog - Weebly Beginners Guide
For instructions on how to edit and add blog posts to your blog click on this link. Blogs & Forums
Navigate to this website for more tips on creating a Weebly web page and blog - Weebly Beginners Guide
Exercise
Download and print the file below and complete the exercise.
| dct_exercise_4.pdf | |
| File Size: | 168 kb |
| File Type: | |
Social Media - Creating and Using Social Media
Social Media has taken the world by storm, sites such as Facebook, Twitter, MySpace, Bebo all allow users to converse with friends and family, upload and share photos and make friends and connections all over the world. We are primarily going to look at Facebook in this example but many of these conventions apply to all social media.
Social Media Conventions
- Introducing yourself properly. Social Networking is no different to socialising in person, when asking to be friends with someone it is still polite to introduce yourself.
- Do not have private conversations in public. On Facebook, your wall is the most commonly used area, you can have conversations with people here however avoid using this for conversations that are private or may insult/hurt someone else. Use the private message option. This is the same as an email message.
- Uploading & Tagging Photos. Be careful of what photos you upload to facebook, embarrassing photos of you and your friends can impact your life in the future. Photos that you upload also become the property of facebook as stated in their terms and conditions. Avoid tagging your friends in photos that may embarrass them, let them tag themselves so it is their choice.
- Be careful what you post! Posts can be removed from sight however this does not mean they have been removed from the internet all together. Think before you make comments as you may regret these at a latter date. Think about what implication your comments may have on others also. being that social networking is all about links between people. Something you say can easily get around.
- Accept requests only from people you know. You do not have to accept every person who requests your friendship. Take a minute to think, why would a complete stranger want to add me on Facebook as a friend.
Facebook Explained
Signing Up to Facebook
Other Social Media
There are many forms of social media all providing different spins on networking with others. Below we are just touching on a few other options.
Twitter Explained
Visit this website for more information on Twitter at Mashable
FourSquare Explained
Skype Explained
How to use and sign up to Skype
To sign up to skype, click on this link: Skype sign up
You will not have to install skype on the Otago Polytechnic computers, however if you wish to install it at home follow these instructions.
You will not have to install skype on the Otago Polytechnic computers, however if you wish to install it at home follow these instructions.
Exercise
Download and print the file below and complete the exercise.
| dct_exercise_5.pdf | |
| File Size: | 166 kb |
| File Type: | |
Inappropriate use of DCTs
With all forms of communications there is the risk that they will be used in an inappropriate manner. This is the same with DCTs, both businesses and individuals need to be aware of their responsibilities and the protocols which should be followed.
Business
When talking about DCTs in a business context we must understand when it is appropriate to use them. DCTs should not be used during a meeting unless it is required to fulfill the purpose of the meeting, texting or sending emails whilst in a meeting is both disrespectful to the other participants and also disruptive.
Using DCTs to transmit sensitive information also needs consideration. Bearing in mind how easy it is for information to be sent to the wrong person, we must make the best choice for the situation and content of the communication. |
http://advantagebizmag.com/archives/2384
|
Personal
Due to the availability of DCTs in every day life it has become more common place for people to use DCTs a lot of the time. However this does not make is ok. We still must respect others when using DCTs. Using cellphones or net books in a movie theater would interrupt the viewing pleasure of other movie goers. Also if you are in a important conversation with someone it is not good practice to pull your phone out and start sending a SMS or updating your status on Facebook.
It is important to remember that when you are take a phone call, send a text message or send an email whilst in a conversation with someone else it makes them feel less important. |
http://www.textually.org/textually/archives/2009/02/022817.htm
|
Time & Cost
Time is a important factor of using DCTs. With the example of SMS and MMS the time in which you send a message can have an affect on the person you are sending it to. This can also be the case in business sense, people may only want to deal with business related work during business hours. Even though DCTs allow us to communicate with and access people at any time,it is important take time into consideration.
Cost is another aspect of DCTs that must be considered. The cost of using DCTs can very in different countries based on the plans that the consumer has signed up for with the device. When traveling overseas the costs of using DCTs increases as consumers must use the global roaming feature. This charges the consumer to receive calls and data. To avoid high costs it is best for the consumer to select a plan (Number of SMS, Call minutes and Data) that best suits their needs.
Cost is another aspect of DCTs that must be considered. The cost of using DCTs can very in different countries based on the plans that the consumer has signed up for with the device. When traveling overseas the costs of using DCTs increases as consumers must use the global roaming feature. This charges the consumer to receive calls and data. To avoid high costs it is best for the consumer to select a plan (Number of SMS, Call minutes and Data) that best suits their needs.
Things to Remember
Be Polite: If you need to take a call then excuse yourself from your conversation.
Think about others: Take into consideration what impact on others your use of DCTs might have.
Think before you click: Before sending off a message,making a call, etc think about the implications. what time is it, what are you communicating.
Consider the Cost: The cost of communication alwasy needs to be considered exspecailly with using Roaming features.
Think about others: Take into consideration what impact on others your use of DCTs might have.
Think before you click: Before sending off a message,making a call, etc think about the implications. what time is it, what are you communicating.
Consider the Cost: The cost of communication alwasy needs to be considered exspecailly with using Roaming features.
Ethical and Legal Issues associated with the use of DCTs
With the rapid increases and changes in technology of DCTs, we must consider the legal and ethical issues that arise from the the new found accessibility of communication.
Cyber/Text - Bullying and Stalking
|
Cyber/Text bullying has become a serious issue in today's world of DCTs. The term cyber/text bullying means when one person uses a DCT to send hateful, embarrassing, or menacing messages to another person. This act often occurs with teenagers under the age of 18 however is becoming more common with younger kids as they start using DCTs at younger ages.
Cyber/Text Stalking is slightly different. This term refers to the actions of someone usually over the age of 18 who uses DCTs to pester another person with messages and phone calls or uses DCTs to keep track of your actions and movements. Cyber/Text bullying and stalknig can have server and detrimental effects on individuals, some say cyber/text bullying and stalking is worse than being bullied or stalked in person due to the ease of access to DCTs and the ability to harass and menace 24/7. Users of DCTs need to be aware that using DCTs for purposes like bullying and stalking is an illegal action and could find them selves with fines or imprisonment placed upon them. |
http://stufffromthelab.wordpress.com/2007/04/13/cyber-bullying-what-is-it/
|
Privacy
Privacy is the right for an individual or organisation to control access over their own information.
Copyright
The Copyright Act 1994 along with its most recent amendments set out the rights and restrictions around the copying of information in New Zealand. Copyright literally means 'the right to copy', any original work which is created, published or performed is subject to copyright. The creator be it an organisation or an individual has exclusive rights to reproduce, scan, record, download and or store, publish, distribute, perform and adapt their work. In most cases the creator of the work is the owner and copyright holder, the exceptions to this are below:
In the example of computer software, producers often apply Copyright Notices or Licences that limits the use of the software to one computer and prevents the copy of the software. The consequences of breaking Copyright law can be severe - up to 5 years in jail or a fine of $150,000. In the event of breach of Copyright, managing directors or business owners can be held responsible.
More information on the Copyright Act 1994 can be found on this website: Copyright Act 1994
- When an employee creates a work for their employer, the copyright belongs to the employer.
- When any work is commissioned or paid for by a second party, the copyright belongs to the party who paid for the work to be created.
In the example of computer software, producers often apply Copyright Notices or Licences that limits the use of the software to one computer and prevents the copy of the software. The consequences of breaking Copyright law can be severe - up to 5 years in jail or a fine of $150,000. In the event of breach of Copyright, managing directors or business owners can be held responsible.
More information on the Copyright Act 1994 can be found on this website: Copyright Act 1994
DCTs have had a substantial impact on the need for changes to the copyright laws in New Zealand and around the world. Advances in the internet and file sharing programs has increased the ability to share, music, videos, programs and other files with other people free of charge to the party receiving the file. This is in direct breach of copy right as the author of the file is not receiving and payment for the work.
Spam
Apart from the fact that it is a nuisance, and that it may advertise objectionable content, spam can also be a security threat. Many spam emails contain Web bugs; these are invisible graphics containing trac king code designed for the same purposes as spyware. Additionally the amount of spam and the frustration of having to deal with it may lead users to behave with less than usual suspicion, and for that reason it can be used to deliver a virus, spyware or phishing scams.
To manage spam: Don't open spam email, or email from people you do not know.
Get a free web-based email address from sites like Mail.com, Yahoo or Lycos mail, and use it when you sign up for Web sites or fill in forms online. Make sure when you sign up for free email, that you don’t agree to have your address shared with other parties. You needn’t be truthful about your personal details either.
To manage spam: Don't open spam email, or email from people you do not know.
Get a free web-based email address from sites like Mail.com, Yahoo or Lycos mail, and use it when you sign up for Web sites or fill in forms online. Make sure when you sign up for free email, that you don’t agree to have your address shared with other parties. You needn’t be truthful about your personal details either.
Malware
'Malware' is a short for malicious software, it includes any sort of software that is used to gain unauthorised access to a computer system.
For information on Viruses, Trojans and other threats. Go to the internet course and look for Threats on the internet.
Identity Theft
Identity theft is the act of pretending to be someone you are not to either gain information, money or benefit in another way. DCTs have allowed fraudulence people to access this information easier than ever before. Below we have listed ways people can gain information.
- Using malware to access secret information like passwords through the use of key logging programs.
- Personal data that can be removed from DCTs after being sold or thrown away.
- Hacking into computer networks, systems and databases to obtain personal data.
- Impersonating trusted organisations (e.g. Microsoft, Apple etc) to trick people into revealing information.
Exercise
Download and print the file below and complete the exercise.
| dct_exercise_6.pdf | |
| File Size: | 166 kb |
| File Type: | |
Preventing and Responding to DCT Threats
Cyber-bullying and Stalking
The best way to prevent and reduce the amount of cyber bullying and stalking is education. Educating children on correct use of DCTs and the consequences if they chose not to use them correctly. These consequences could include losing their ISP or IM accounts, losing their DCTs or even the possibility of criminal charges which can result in fines or even prison time. This education will help children to think twice before sending cyber bullying messages, often children don't think before sending something that may hurt the recipient of the message and even if the sender did not mean to bully, the damage is already done.
It is important to block the cyber-bully so that they can't send messages to you and or your children. The leading Communication companies in New Zealand have avenues to prevent bullying and stalking for example Vodafone has created a service to try and reduce this negative reality of DCTs.
Visit Vodafones websites below for more information on SMS bullying:
SMS/Text Bullying
Vodafone Blacklist
Reporting the bully or stalking to someone in authority is also a good way to deal with a bully as a child. Support is available online at www.stopcyberbullying.org/.
It is important to block the cyber-bully so that they can't send messages to you and or your children. The leading Communication companies in New Zealand have avenues to prevent bullying and stalking for example Vodafone has created a service to try and reduce this negative reality of DCTs.
Visit Vodafones websites below for more information on SMS bullying:
SMS/Text Bullying
Vodafone Blacklist
Reporting the bully or stalking to someone in authority is also a good way to deal with a bully as a child. Support is available online at www.stopcyberbullying.org/.
Privacy and Identity TheftThere are a number of different threats to privacy and risks related to identity theft.
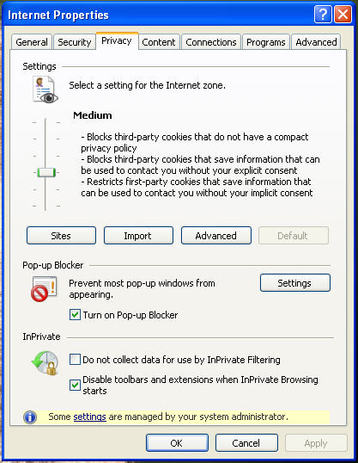
Cookies When you use internet explorer as your internet browser this program allows the user to specify their privacy settings under the internet options. These options allow you to adjust the level of security that allows cookies to access your system. To protect your privacy and reduce the risk of identity theft, set your security between high and medium. Phishing
This act is an attempt to get your personal information through the misrepresentation of a trusted source. Often this is done via a fake website that looks the same as an official website in the hope you will trust this organisation enough to provide personal details or log in information to accounts etc. Phishing is often done via email also, always check email addresses and company logos to ensure that it is the actual firm. |
Personal Disclosure
Many people are unaware of the amount of information about them that is stored online. Many young people post personal information or photos online through social networking sites without being aware of the full implications of posting such information. For example posting personal information in chat rooms and blogs allows anyone who has access to these site access to your information. A prime example is the social networking site Facebook. most users are unaware that any information you post on facebook become the rights of facebook so any personal information you post on there becomes property of facebook and they can distribute that information.
Protecting your identity online
Many people are unaware of the amount of information about them that is stored online. Many young people post personal information or photos online through social networking sites without being aware of the full implications of posting such information. For example posting personal information in chat rooms and blogs allows anyone who has access to these site access to your information. A prime example is the social networking site Facebook. most users are unaware that any information you post on facebook become the rights of facebook so any personal information you post on there becomes property of facebook and they can distribute that information.
Protecting your identity online
- A blog is for life - Remember you risk leaving a permanent electronic footprint. If you don't think you'll want it to exist somewhere in a years time, don't post it.
- Privacy is precious - choose sites that give you plenty of control over who can find your profile and how much information they can see. Read privacy policies and understand how the sites will use your details.
- Personal safety first - don't allow people to work out your 'real life' location eg your place and hours of work. Your personal safety offline could be affected by what you tell people online.
- Password protected - change your password regularly, don't use obvious words like your pets names and don't use the same passwords on social networking sites as you do things like internet banking.
- Address aware - use a separate email address for social networking sites.
Malware
Simple suggestions for keeping your system and data safe from malware like viruses, trojans, worms and spyware.
Simple suggestions for keeping your system and data safe from malware like viruses, trojans, worms and spyware.
- Buy and install anti virus software, Its is advised to purchase full anti virus rather than download a free one as the free software does not have the same level of protection that a fully licences purchased version does.
- Don't let others use their external devices in your computer unless you have scanned the drives for viruses.
- Virus check your system regularly.
- Update your virus protection software on a regular basis.
- Only open files that are from trusted sources.
If you think your computer has contracted a virus or malware. First conduct a virus scan with your anti virus software. If your antivirus has identified malware then disconnect from any network so the virus cannot spread and then malware removal software before reconnecting to any network.
Preventing Spam
Preventing Spam
- Make suer you have a firewall in place and operating. (almost every computer comes with an operational firewall unless custom built)
- Check the junk mail or spam settings in your email program
- Be careful about where you post your email address
- Check all tick box's when signing up to services
Responding to Spam
- Never reply to spam (delete it as soon as you find it in your email)
- Never forward chainmail
Exercise
Download and print the file below and complete the exercise.
| dct_exercise_7.pdf | |
| File Size: | 166 kb |
| File Type: | |